II. Clients for the date & echo services:
- Note most of the below doesn't work these days, because services have been turned off.
- This is due to security concerns.
- I've left the below in for you to see anyway as example clients, it's just that you aren't going to get to run them & try it yourself.
- Unless you download (or write) a service server yourself and run it on your own machine!
- Note to lecturer: this lecture combines two old ones & so runs long
- go through this quickly for history, but basically skip the clients and get to the line server, demo telnet off of that.
- probably showed /etc/services in
the previous lecture.
- In order to make clients and servers more clear to you,
here are some examples based on standard services.
- The example servers are standard internet services, which are provided by at least unix / linux computers.
- Standard services have standard port numbers.
- On unix machines (including mac OS X) you can find these in /etc/services
- There is also an internet site detailing all standard port-number assignments.
- From that page:
The port numbers are divided into three ranges: the Well Known Ports,
the Registered Ports, and the Dynamic and/or Private Ports.
The Well Known Ports are those from 0 through 1023.
DCCP Well Known ports SHOULD NOT be used without IANA registration.
The registration procedure is defined in [RFC4340], Section 19.9.
The Registered Ports are those from 1024 through 49151
DCCP Registered ports SHOULD NOT be used without IANA registration.
The registration procedure is defined in [RFC4340], Section 19.9.
The Dynamic and/or Private Ports are those from 49152 through 65535 - So when you pick a port for your own application, pick one bigger than 49152!
- The example client is a program called telnet,
which is a generic client which can connect to any
service.
- The thing is, you have to type in the side of the protocol that the server expects.
- That's because telnet (being generic) won't know about it.
- So you are kind of being a fake client, and telnet is
just helping you out.
- Since there are a lot of different actors in these examples I'm using colour coding.
- Sorry if you are colour blind. You can try looking at the html source to see which colours I used!
- Green is me.
- Blue is the telnet program.
- Reds & oranges are the servers (there are different ones.)
- Black is the unix shell. (the operating system)
- Here I am turning the services on & talking to them
on for my linux box:
[root@sydney etc]# telnet localhost 7
Trying 127.0.0.1...
telnet: connect to address 127.0.0.1: Connection refused
[root@sydney etc]# /sbin/chkconfig daytime on
[root@sydney etc]# telnet localhost 15
Trying 127.0.0.1...
telnet: connect to address 127.0.0.1: Connection refused
[root@sydney etc]# less services # this let me see what the different services were & find the right number
[root@sydney etc]# telnet localhost 13
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
17 MAR 2004 21:50:15 GMT
Connection closed by foreign host.
[root@sydney etc]# less services
[root@sydney etc]# /sbin/chkconfig echo on
[root@sydney etc]# telnet localhost 7
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
hi
hi
golf
golf
^] - Notice a couple of things here:
- I've tapped into the server with a program called "telnet".
- Telnet basically just lets you talk to
ports directly.
- It used to be used to login for sessions, but it's too insecure. Nowadays we use ssh instead.
- I'll be showing you how you can use telnet to fake internet / application protocols in a couple weeks (assuming *that* hasn't been shut down).
- Mostly because of security, but also because in class I won't be networked, I'm talking to my own machine as if it's a machine on the internet.
- Your own machine can be accessed with the special IP address 127.0.0.1
- it's DNS name is "localhost" (as well as any other name you've given it.)
- Again, I'll probably explain DNS & how the
internet routes packets in two weeks.
- I happen to be in the /etc directory, so the file that tells you the right port number for things is just "services".
- I have to be root to turn the services on.
- More
hacky notes like these are here.
- The first server, daytime (port 13), kicked me out after giving me the information it gives.
- I didn't have to type anything at all.
- very simple protocol.
- The second server, echo (port 7) responded to what
I typed.
- But there's no way to quit it!
- To quit I had to talk to telnet directly, so I had to
type the telnet escape command, ^].
- Assuming
you can find a computer that will let you talk to its
daytime server, then you can run this program (which is
taken with only a slight modification from Object-Oriented
Programming
with Java by David
Barnes, Chapter 19 (on Networking!):
import java.net.*;
import java.io.*;
// Contact the daytime server running on hostname.
public class DaytimeClient {
// Contact the server at the appropriate port and set
// the socket attribute for the run() method to use.
public DaytimeClient(String hostname) throws Exception {
// The well-known port of the TCP daytime service.
final int DaytimePort = 13;
try{
socket = new Socket(hostname,DaytimePort);
}
catch(UnknownHostException e){
throw new Exception("Unknown host: "+e.getMessage());
}
catch(IOException e){
throw new Exception("IOException on socket creation: "+e.getMessage());
}
}
// Obtain the time of day from the daytime server.
public void run() {
Socket daytime = getSocket();
try{
// Get the stream used by the server to send data.
InputStream inStream = daytime.getInputStream();
// Wrap the stream in a BufferedReader.
BufferedReader reader = new BufferedReader(
new InputStreamReader(inStream));
// The server will only send a single line.
String response = reader.readLine();
System.out.println(response);
// Close the connection now it is finished with.
daytime.close();
}
catch(IOException e){
System.err.println(e.getMessage());
}
}
protected Socket getSocket(){
return socket;
}
private final Socket socket;
public static void main(String[] args) {
if(args.length == 1){
try{
DaytimeClient client = new DaytimeClient(args[0]);
client.run();
}
catch(Exception e){
System.err.println("Exception: "+e.getMessage());
}
}
else{
System.err.println("You must supply the name of a host to contact.");
}
}
} - Here's one that talks to echo...
/* author david barnes & joanna bryson
*
*/
import java.net.*;
import java.io.*;
// Contact the echo server running on hostname.
class TCPEchoClient {
// Contact the server at the appropriate port and set
// the socket attribute for the run() method to use.
public TCPEchoClient(String hostname) throws Exception {
try{
// The well-known port of the TCP echo service.
final int EchoPort = 7;
socket = new Socket(hostname,EchoPort);
}
catch(UnknownHostException e){
throw new Exception("Unknown host: "+e.getMessage());
}
catch(IOException e){
throw new Exception("IOException on socket creation: "
+e.getMessage());
}
}
protected Socket getSocket(){
return socket;
}
private final Socket socket;
public static void main(String[] args) {
try {
TCPEchoClient eClient = new TCPEchoClient("localhost");
// now you know stdin is really a socket too!
BufferedReader stdin =
new BufferedReader(new InputStreamReader(System.in));
String myEchoString;
System.out.print("Welcome to the echo client. The prompt looks like >>."
+ "\n >> ");
// Wrap the input stream in a BufferedReader.
BufferedReader reader = new BufferedReader(
new InputStreamReader(eClient.getSocket().getInputStream()));
// Wrap the output stream in a BufferedWriter.
BufferedWriter writer = new BufferedWriter(
new OutputStreamWriter(eClient.getSocket().getOutputStream()));
// read a string from stdin & send it to echo
while ((myEchoString=stdin.readLine()) != null) {
System.out.println("Sending: "+myEchoString);
writer.write(myEchoString);
writer.newLine();
// Make sure the data is flushed to the stream.
writer.flush();
// Read the response.
String response = reader.readLine();
System.out.println("The response is: "+response);
System.out.print("\n >> ");
} // while strings
// Close the connection
eClient.getSocket().close();
}
catch(IOException ioe){
ioe.printStackTrace();
}
catch(Exception e) {
e.printStackTrace();
}
} // main()
} // class TCPEchoClient - Sorry I didn't color those creatively, but if you look at them in emacs (or eclipse) it should color them for you.
- If your BUCS
unix server emacs isn't making pretty colors for you,
you should put this in your .emacs file
; stick colour in old versions of emacs --
;; Are we running XEmacs or Emacs?
(defvar running-xemacs (string-match "XEmacs\\|Lucid" emacs-version))
;; Turn on font-lock mode for Emacs
(cond ((not running-xemacs)
(global-font-lock-mode t)
))
; -- ( colour stuff from Adam Dziedzic ) -- - Notice: emacs is
written in lisp!
- You might want
to look at ~cssjjb/.emacs for more random stuff
III. Servers
- As mentioned in Lecture 10, servers:
- have to start running first.
- need a port to listen for clients on.
- But once a server has made the connection to the client, it's really just the same.
- Here is yet more code from David Barnes -- this time I
left the main as he wrote it (in another class) though I
really don't see the advantage... (so no comment claiming
I'm a coauthor!)
- The server class
import java.net.*;
import java.io.*;
// A simple server that accepts a client connection
// and sends back the length of the strings it
// receives from the client.
class LineLengthServer {
public LineLengthServer(int port) throws Exception {
try{
// Listen on the given port.
serverSocket = new ServerSocket(port);
}
catch(BindException e){
throw new Exception("Failed to create a server socket: "+
e.getMessage());
}
}
// Read strings and return their length (as a String)
// to the client.
public void run() throws Exception {
ServerSocket serverSocket = getServerSocket();
Socket clientSocket = null;
try{
System.out.println("Listening for a client on port: "+
serverSocket.getLocalPort());
// Wait for a client to make contact.
clientSocket = serverSocket.accept();
// Contact ...
System.out.println("A client has arrived.");
// Wrap the input stream in a BufferedReader.
BufferedReader reader = new BufferedReader(
new InputStreamReader(clientSocket.getInputStream()));
// Wrap the output stream in a BufferedWriter.
BufferedWriter writer = new BufferedWriter(
new OutputStreamWriter(clientSocket.getOutputStream()));
// Read lines until the client terminates.
String request = reader.readLine();
while(request != null){
// Write the length of the line as a String.
writer.write(String.valueOf(request.length()));
writer.newLine();
writer.flush();
request = reader.readLine();
}
}
catch(IOException e){
throw new Exception("IOException talking to the client: "+
e.getMessage());
}
finally{
if(clientSocket != null){
System.out.println("The client has gone.");
// Close the socket to the client.
clientSocket.close();
}
}
serverSocket.close();
}
protected ServerSocket getServerSocket(){
return serverSocket;
}
// The socket on which the listening is done.
private final ServerSocket serverSocket;
} - The "main" class
// An example of a simple server that reads lines from
// clients and sends back the length of each line
// it receives.
public class LineLengthServerMain {
public static void main(String[] args){
try{
// An arbitrary port number to listen on. This should be
// larger than 1024 for user-written servers.
final int port = 24101;
LineLengthServer server = new LineLengthServer(port);
server.run();
}
catch(Exception e){
System.err.println("Exception: "+e.getMessage());
}
}
} - Running it from linux
[joanna@sydney Networks]$ javac LineLengthServerMain.java
[joanna@sydney Networks]$ java LineLengthServer
Exception in thread "main" java.lang.NoSuchMethodError: main
[joanna@sydney Networks]$ java LineLengthServerMain
Listening for a client on port: 24101
^Z
[2]+ Stopped java LineLengthServerMain
[joanna@sydney Networks]$ bg
[2]+ java LineLengthServerMain &
[joanna@sydney Networks]$ telnet localhost 24101
Trying 127.0.0.1...
A client has arrived.
Connected to localhost.
Escape character is '^]'.
hi there
8
have you ever thought
21
this isn't really measuring the line length...
46
Ah ha!
6
^]
telnet> .
?Invalid command
telnet> quit
Connection closed.
The client has gone.
[2]+ Done java LineLengthServerMain
[joanna@sydney Networks]$ - Notice I used telnet as a client again (see colour code mentioned earlier).
- And also, I suspended the server process (with ^Z) and then backgrounded it by typing bg
- This made it start running run, but leaving me STDIN to use with telnet.
- You can also type fg and get right back where you were.
- You could also start
the server in the background in the first place by
typing an & afterwards like this: j2bryson$ java
LineLengthServerMain &
- Note both
programs now shared STDOUT!
- Consequently, both programs were printing to the screen at the same time -- telent I made blue, the server red, and what I typed green.
- I also forgot the telnet protocol / commands -- I thought you killed it with a .
- mail quits with a .
- I got it right the second guess though.
- Don't be
afraid to hack!
- If you want to make a server accept more than one connection, just put a while loop in so it looks again (see the outlined server back in section I.)
- If you want to have the server accept new clients while it's still servicing old ones, you need to use threads!
- You
need this for coursework 2.
- Here's an example of that, again from Barnes (hey, he
writes good examples! This is from RandomServiceListener)
public void listen() throws Exception {
ServerSocket serverSocket = getServerSocket();
// Wait up to 30 minutes for new clients.
final int timeToWait = 1*60*1000;
boolean keepWaiting = true;
while(keepWaiting){
try{
// Wait for a client to make contact.
serverSocket.setSoTimeout(timeToWait);
Socket clientSocket = serverSocket.accept();
// Let a separate Thread handle it. QUIZ why are there 2 news?
new Thread(new RandomService(clientSocket)).start();
}
catch(InterruptedIOException e){
// We timed out waiting for a client.
keepWaiting = false;
}
catch(IOException e){
throw new Exception("IOException: "+ e.getMessage());
}
}
// No more clients, so close the socket.
serverSocket.close();
} - Notice not only the threading, but the fact it handles interupts, so it can eventually be killed!
- It also sets a timeout so that it will effectively interrupt itself if it's been waiting too long (as well as accepting terminate signals, e.g. from the keyboard.)
- it also creates a Thread object just to access "start"
(answer to quiz)
IV. Protocols
- A protocol is a system / procedure for communicating between two computers.
- As with military & diplomatic protocols, it's designed to make certain that mistakes or misunderstandings don't happen.
- Computers are even stupider than people, so computer protocols have to be followed very precisely.
- For both humans and computers, failure to follow correct protocol is one way to spot intruders.
- Example from "From
Russia with Love"
- James
Bond: Pardon me, do you have a match?
Agent: I use a lighter.
James Bond: Better still.
Agent: Until they go wrong.
James Bond: Exactly.
- Actually, in the movie, this protocol is run several times, with Bond taking the part of either agent.
- The purpose of the protocol is for two agents who don't know each other to make certain they are talking to the right person before they reveal anything.
- It doesn't matter which agent goes first, what
matters is
- that the conversation could be started with
anyone, but
- it would be unlikely to be completed correctly
except by another program / agent that is running
the same protocol.
- In computers, protocols happen at many different levels simultaneously
- From freesoft.org's
tutorials:
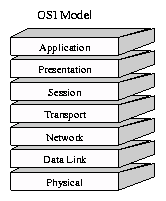
The seven layers of the OSI Basic Reference Model are (from bottom to top):
- The Physical Layer describes the physical properties of the various communications media, as well as the electrical properties and interpretation of the exchanged signals. Ex: this layer defines the size of Ethernet coaxial cable, the type of BNC connector used, and the termination method.
- The Data Link Layer describes the logical organization of data bits transmitted on a particular medium. Ex: this layer defines the framing, addressing and checksumming of Ethernet packets.
- The Network Layer describes how a series of exchanges over various data links can deliver data between any two nodes in a network. Ex: this layer defines the addressing and routing structure of the Internet.
- The Transport Layer describes the quality and nature of the data delivery. Ex: this layer defines if and how retransmissions will be used to ensure data delivery.
- The Session Layer describes the organization of data sequences larger than the packets handled by lower layers. Ex: this layer describes how request and reply packets are paired in a remote procedure call.
- The Presentation Layer describes the syntax of data being transferred. Ex: this layer describes how floating point numbers can be exchanged between hosts with different math formats.
- The Application Layer describes how real work actually gets done. Ex: this layer would implement file system operations.
The original Internet protocol specifications defined a four-level model, and protocols designed around it (like TCP) have difficulty fitting neatly into the seven-layer model. Most newer designs use the seven-layer model.
- Actually having this many layers of protocol is
controversial, because it may slow things down, and it's
unclear that it brings much advantage.
- The five-layer TCP/IP
model skips the presentation & session layer
above.
- But it is useful to have at least a few layers, e.g.
- The machine / hardware layer (get the bits into the right format for the wires / computer).
- The communication / networking layer, on the internet
typically TCP/IP (check & route the packets).
- The application layer.
- Application protocols are often human readable so that they can be debugged. But lower level protocols are only for machines.
- Java's basic sockets provide a connection-oriented protocol which will make sure no data is lost for you.
- connection is maintained even when no data is going down it.
- In particular, Java uses TCP (the Transmission Control Protocol).
- This works on top of IP (the Internet Protocol) which is what handles the packets
- are little chunks the data gets broken into so
no big / slow chunk risks getting lost or blocking other
actions
- packets include some other useful information such as the address they're going to.
- having the apacketsddress in every packet is redundant, so the size of packets has to be traded off with other networking considerations.
- An example of a human-readable protocol is the Send Mail Transfer Protocol (SMTP). You sometimes see parts of it in messages that have bounced.
- You can also use it through telnet (see the last networking lecture for
more on telnet!)
- Here's an example of me forging mail to myself, from my other (older) self.
- I start out trying to be Elvis, but the mail server is
on to this trick these days!
[jjb@jjb op.papers]$ telnet XXXXX 25
Trying 138.38.108.3...
Connected to XXXXXXXXX.ac.uk (138.38.XXX.XXX).
Escape character is '^]'.
220 XXXXXXXXX.ac.uk ESMTP Exim 4.30 Tue, 16 Mar 2004 08:00:12 +0000
HELP
214-Commands supported:
214 AUTH HELO EHLO MAIL RCPT DATA NOOP QUIT RSET HELP
RCPT TO: jjb@cs.bath.ac.uk
503 sender not yet given
MAIL FROM: elvis@graceland.com
250 OK
RCPT TO: jjb@cs.bath.ac.uk
550 RFCs mandate HELO/EHLO before mail may be sent
HELO
501 Syntactically invalid HELO argument(s)
HELP HELO
214-Commands supported:
214 AUTH HELO EHLO MAIL RCPT DATA NOOP QUIT RSET HELP
HELO jjb.cs.bath.ac.uk
250 air.cs.bath.ac.uk Hello jjb.cs.bath.ac.uk [138.38.108.1]
RCPT TO: jjb@cs.bath.ac.uk
503 sender not yet given
MAIL FROM: elvis@kingdom.co
250 OK
RCPT TO: jjb@cs.bath.ac.uk
550-Verification failed for
550-Unrouteable address
550 Sender verify failed
RCPT FROM: joanna@ai.mit.edu
500-unrecognized command
500 Too many syntax or protocol errors
Connection closed by foreign host.
[jjb@jjb op.papers]$ telnet XXXXXX 25
Trying 138.38.108.3...
Connected to XXXXXXXXX.ac.uk (138.38.XXXXXX).
Escape character is '^]'.
220 air.cs.bath.ac.uk ESMTP Exim 4.30 Tue, 16 Mar 2004 08:04:01 +0000
HELO jjb.cs.bath.ac.uk
250 air.cs.bath.ac.uk Hello jjb.cs.bath.ac.uk [138.38.108.1]
RCPT TO: jjb@cs.bath.ac.uk
503 sender not yet given
MAIL FROM: joanna@ai.mit.edu
250 OK
DATA
503 valid RCPT command must precede DATA
RCPT TO: jjb@cs.bath.ac.uk
250 Accepted
DATA
354 Enter message, ending with "." on a line by itself
Hi Dr. Bryson, this is me pretending to be myself at MIT.
.
250 OK id=1B39ZG-0004yz-DU
quit
221 XXXXXXXXXX.ac.uk closing connection
Connection closed by foreign host.
(and then in my mail spool I got...)
Return-Path:
Received: from air ([unix socket])
by air (Cyrus v2.1.15) with LMTP; Tue, 16 Mar 2004 08:05:15 +0000
X-Sieve: CMU Sieve 2.2
Return-path:
Envelope-to: jjb@cs.bath.ac.uk
Delivery-date: Tue, 16 Mar 2004 08:05:15 +0000
Received: from [138.38.108.1] (helo=jjb.cs.bath.ac.uk)
by air.cs.bath.ac.uk with smtp (Exim 4.30)
id 1B39ZG-0004yz-DU
for jjb@cs.bath.ac.uk; Tue, 16 Mar 2004 08:05:15 +0000
X-Spam-Score: 2.9 (++)
Hi Dr. Bryson, this is me pretending to be myself at MIT. - Notice this doesn't actually mention joanna@ai.mit.edu -- although I needed a valid address to send mail, it didn't get stuck into the Return-Path
- I probably could have put it in with a few more arguments buried in the DATA.
- But that wouldn't have generated a full path through the internet.
- This is something spam assassin looks for! Notice I got a high spam score without saying any bad words.
- This example was run in 2004 -- in lecture I'll show you that it's not much different in 2010.
- No I won't – by 2014 the security folks notice
if a machine is using their mailer but isn't in their
domain.
- The interesting thing is that the SMTP protocol is only the numbers & letters + their arguments.
- You know there can be many different mail clients that use this protocol, you've probably used a few different ones (pine, gmail, outlook, mail).
- People can also write different servers! For
example, here's the mail server that's built into my Linux
laptop (Redhat 9)
[joanna@sydney CM10135]$ telnet localhost 25
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
220 localhost.localdomain ESMTP Sendmail 8.12.8/8.12.8; Thu, 18 Mar 2004 14:08:45 GMT
HELO cs.bath.ac.uk
250 localhost.localdomain Hello localhost.localdomain [127.0.0.1], pleased to meet you - The geeks who wrote this program chose to add ", pleased to meet you" after the formal protocol, because the spec told them it didn't matter what they said.
- Or possibly the geeks that wrote the other mailer chose to drop that part off, so it would look more professional, knowing that no one bothered to parse that bit.
- Either way, the point is that the
protocol is what matters, the clients &
servers can change as long as they observe it.
- You may also want to look at this lecture on internet applications from Dave Hollinger
V. How Internet Addressing Works
- See the Wikipedia entry in IP Addresses.
- Here are some great lecture notes on IP Addresses & DNS for Java (in PDF), and some decent ones on the Architecture of the Internet (in HTML).
- Internet invented by Al Gore, no seriously, by Larry Roberts & Tom Merrill (see the Brief History of the Internet)
- who in 1965 connected a computer at MIT with one from Stanford (? CA anyway, maybe some DARPA lab),
- they invented the idea of breaking data into packets & resending ones that got lost.
- Most research was funded by the US Military, "ARPANET"
- so the government could survive nuclear war.
- very decentralized -- any computer that gets a packet
knows how to send it to another computer that can
- Larry Roberts also invented email in 1972.
- MILNET (for the US military) & ARPANET split in 1983, the same time as TCP/IP was adopted as main protocol
- 1983 is also when I got my first email account,
coincidently.
- When we used to use email in the 80's, email took a day to get around the world.
- We thought this was amazing!
- Links in the internet phoned each other maybe once every hour or two to see if there were any bits to send.
- Al Gore did help get a lot of US taxpayer money into developing/expanding the Internet for commercial use --- politics does matter.
- Internet addresses currently are four 8-bit numbers (so
each goes up to 28, or 256), so there can be
4,294,967,296 unique IP addresses --
probablynot enough for 7,000,000,000 people! - Getting a packet to the right place:
- first get it to a machine that matches the first number,
- that machine should be able to get it to a machine that matches the second number...
- so routers only need to know how to get to 4*256 machines, (1024), not 4 billion.
- logarithmic! divide & conquer!
- Traceroute will show you how packets have to travel --- again, if you can find a machine that still runs it (I had to go to MIT... in 2004!)
- It works from a coffeeshop in 2014, but is weirdly slow. But below is the 2004
one.
/home/ai/joanna % traceroute cs.bath.ac.uk
traceroute to cs.bath.ac.uk (138.38.108.2), 30 hops max, 40 byte packets
1 net-chex (128.52.37.10) 1 ms 1 ms 1 ms
2 anacreon (128.52.0.10) 2 ms 3 ms 1 ms
3 radole (18.24.10.3) 2 ms 76 ms 74 ms
4 B24-RTR-2-LCS.MIT.EDU (18.201.1.1) 70 ms 109 ms 72 ms
5 EXTERNAL-RTR-2-BACKBONE.MIT.EDU (18.168.0.27) 89 ms 105 ms 87 ms
6 MIT-GIGAPOPNE.nox.org (192.5.89.89) 95 ms 84 ms 80 ms
7 192.5.89.10 (192.5.89.10) 91 ms 99 ms 98 ms
8 198.32.11.62 (198.32.11.62) 73 ms 118 ms 115 ms
9 ny.uk1.uk.geant.net (62.40.96.170) 175 ms 109 ms 133 ms
10 janet-gw.uk1.uk.geant.net (62.40.103.150) 129 ms 143 ms 148 ms
11 po3-0.lond-scr3.ja.net (146.97.35.133) 150 ms 134 ms 143 ms
12 po6-0.read-scr.ja.net (146.97.33.13) 173 ms 153 ms 163 ms
13 po2-0.bris-scr.ja.net (146.97.33.49) 141 ms 191 ms 201 ms
14 gi0-1.frenchay-bar.ja.net (146.97.35.82) 191 ms 186 ms *
15 146.97.40.198 (146.97.40.198) 156 ms 167 ms 138 ms
16 bath-1-brisf-1-r1.swern.net.uk (194.82.125.50) 138 ms 158 ms 161 ms
17 bath-gw-1-bath-1.swern.net.uk (194.82.125.198) 143 ms 193 ms *
18 earth.cs.bath.ac.uk (138.38.108.2) 174 ms 153 ms 155 ms
19 earth.cs.bath.ac.uk (138.38.108.2) 166 ms 168 ms 171 ms
20 earth.cs.bath.ac.uk (138.38.108.2) 209 ms 184 ms 184 ms - JA is the JANET, the UK's main network.
- It used to be really annoying, because it made all the addresses backwards, e.g. uk.ac.bath.midge
- lots of clients & servers would get confused translating, even though they should have known better
- Mail to ai.mit.edu would wind up in Antigua!
- Moral: Even when there's a clear protocol, making
things too tricky confuses programmers & things
break.
- What about going to Hong Kong?
/home/ai/joanna % traceroute www.hkbu.edu.hk
traceroute to net1.hkbu.edu.hk (158.182.4.1), 30 hops max, 40 byte packets
1 net-chex (128.52.37.10) 1 ms 1 ms 1 ms
2 anacreon (128.52.0.10) 2 ms 1 ms 1 ms
3 radole (18.24.10.3) 2 ms 111 ms 109 ms
4 B24-RTR-2-LCS.MIT.EDU (18.201.1.1) 114 ms 90 ms 118 ms
5 EXTERNAL-RTR-2-BACKBONE.MIT.EDU (18.168.0.27) 118 ms 103 ms 84 ms
6 MIT-GIGAPOPNE.nox.org (192.5.89.89) 91 ms 104 ms 107 ms
7 192.5.89.10 (192.5.89.10) 130 ms 112 ms 126 ms
8 chinng-nycmng.abilene.ucaid.edu (198.32.8.82) 148 ms 162 ms 121 ms
9 iplsng-chinng.abilene.ucaid.edu (198.32.8.77) 123 ms 134 ms 135 ms
10 kscyng-iplsng.abilene.ucaid.edu (198.32.8.81) 146 ms 149 ms 141 ms
11 dnvrng-kscyng.abilene.ucaid.edu (198.32.8.13) 122 ms 150 ms 126 ms
12 snvang-dnvrng.abilene.ucaid.edu (198.32.8.1) 175 ms 137 ms 163 ms
13 losang-snvang.abilene.ucaid.edu (198.32.8.94) 152 ms 153 ms 166 ms
14 tpr2-transpac-la.jp.apan.net (203.181.248.130) 269 ms 276 ms 258 ms
15 taiwan-tpr2.jp.apan.net (203.181.248.153) 290 ms 320 ms 334 ms
16 m160-1-0-0-OC3.tw.ascc.net (140.109.251.42) 308 ms 318 ms 330 ms
17 m20-1-1-0-OC3.hk.ascc.net (140.109.251.45) 360 ms 347 ms 360 ms
18 192.245.196.249 (192.245.196.249) 335 ms 364 ms 383 ms
19 202.40.217.90 (202.40.217.90) 433 ms 457 ms 418 ms
20 202.125.249.5 (202.125.249.5) 385 ms 391 ms 373 ms
21 202.125.249.21 (202.125.249.21) 483 ms 402 ms 453 ms
22 202.125.249.34 (202.125.249.34) 395 ms 382 ms 342 ms
23 158.182.118.73 (158.182.118.73) 478 ms 556 ms 588 ms
24 158.182.118.82 (158.182.118.82) 529 ms 588 ms 620 ms
25 * * *
26 * * *
27 * * *
^C
/home/ai/joanna % - The path out of MIT is the same, but we spend some time on
a big internet
backbone crossing the USA before hopping to Japan,
then Taiwan, then Hong Kong. DNS doesn't have names
for the last few machines!
- That was from 2004 or so --- in 2010 we go directly to HK from asia netcom
- and also, BATH is giving out a lot less dns info!
- This traceroute was taken the day google.cn moved to Hong Kong, note their traceroute is way more efficient (I wonder how they do that?)
- 18 very quick hops...
- 1 fire-private (172.16.0.1) 0.917
ms 0.284 ms 0.318 ms
2 gw (138.38.108.254) 0.814 ms 0.620 ms 0.707 ms
3 swan-wren-10g1.bath.ac.uk (138.38.255.1) 0.852 ms 0.606 ms 0.485 ms
4 4948-bath-bath.swern.net.uk (194.82.120.1) 1.473 ms 1.929 ms 1.464 ms
5 fren-bath-ph.swern.net.uk (194.83.94.64) 2.499 ms 2.211 ms 2.227 ms
6 so-2-1-0.read-sbr1.ja.net (146.97.42.185) 7.771 ms 7.933 ms 8.680 ms
7 so-6-0-0.lond-sbr3.ja.net (146.97.33.166) 9.543 ms 9.148 ms 9.381 ms
8 po1.lond-ban3.ja.net (146.97.35.106) 9.335 ms 9.245 ms 9.193 ms
9 google.lond-ban3.ja.net (193.62.157.30) 9.542 ms 9.740 ms 9.607 ms
10 209.85.252.76 (209.85.252.76) 9.962 ms 209.85.255.175 (209.85.255.175) 9.952 ms 209.85.252.76 (209.85.252.76) 9.870 ms
11 216.239.43.192 (216.239.43.192) 84.140 ms 84.225 ms 84.322 ms
12 209.85.251.233 (209.85.251.233) 98.936 ms 216.239.46.215 (216.239.46.215) 105.018 ms 216.239.46.14 (216.239.46.14) 108.268 ms
13 209.85.241.22 (209.85.241.22) 119.369 ms 121.651 ms 72.14.232.141 (72.14.232.141) 115.884 ms
14 209.85.241.37 (209.85.241.37) 121.752 ms 115.770 ms 209.85.241.29 (209.85.241.29) 117.308 ms
15 209.85.240.45 (209.85.240.45) 120.919 ms 72.14.239.189 (72.14.239.189) 130.899 ms 209.85.240.49 (209.85.240.49) 118.196 ms
16 iw-in-f160.1e100.net (74.125.95.160) 122.741 ms 116.697 ms 122.691 ms - Similarly, here's going from Chapel Arts Centre (in Bath) to Stanford. Note only two hops to get across the USA now, but a bunch to get out of the broadband service (which seems to be run in London)
- mo:~ joanna$ traceroute stanford.edu
traceroute to stanford.edu (171.67.215.200), 64 hops max, 52 byte packets
1 dsldevice (192.168.1.254) 43.776 ms 99.619 ms 99.885 ms
2 host-62-24-255-28.as13285.net (62.24.255.28) 15.632 ms 15.311 ms 16.121 ms
3 host-78-151-230-145.as13285.net (78.151.230.145) 17.602 ms 15.671 ms 15.277 ms
4 host-78-151-230-146.as13285.net (78.151.230.146) 17.988 ms
host-78-151-230-148.as13285.net (78.151.230.148) 16.538 ms
host-78-151-230-154.as13285.net (78.151.230.154) 42.563 ms
5 host-78-144-0-79.as13285.net (78.144.0.79) 19.874 ms
host-78-144-0-75.as13285.net (78.144.0.75) 20.228 ms
host-78-144-11-55.as13285.net (78.144.11.55) 23.467 ms
6 host-78-144-10-68.as13285.net (78.144.10.68) 19.891 ms
host-78-144-10-44.as13285.net (78.144.10.44) 20.071 ms
host-78-144-10-60.as13285.net (78.144.10.60) 23.572 ms
7 v209.core1.lon1.he.net (216.66.84.213) 20.051 ms 28.343 ms 24.892 ms
8 10ge3-1.core1.lon2.he.net (72.52.92.222) 32.591 ms 20.296 ms 20.643 ms
9 100ge1-1.core1.nyc4.he.net (72.52.92.166) 89.471 ms 85.546 ms 86.432 ms
10 100ge7-2.core1.chi1.he.net (184.105.223.161) 112.392 ms 111.764 ms 103.148 ms #chicago
11 10ge11-4.core1.pao1.he.net (184.105.222.173) 160.020 ms 163.949 ms 156.372 ms #palo alto
12 stanford-university.10gigabitethernet1-4.core1.pao1.he.net (216.218.209.118) 155.276 ms 155.860 ms 153.913 ms
13 boundarya-rtr.stanford.edu (68.65.168.33) 158.808 ms 160.090 ms 160.832 ms
14 west-rtr-vlan9.sunet (171.66.255.193) 157.810 ms 165.541 ms 161.424 ms
15 * * *
16 www.stanford.edu (171.67.215.200) 170.619 ms 159.798 ms 158.929 ms
VI. Finding out what your local machine's address is:
- Another useful program potentially for your coursework,
again from David Barnes (the bit that matters is in blue):
// Print out Internet address information about the local machine.
import java.net.*;
public class PrintInetDetails {
public static void main(String[] args){
if(args.length == 0){
try{
InetAddress myDetails = InetAddress.getLocalHost();
System.out.println("The local host is called: "+
myDetails.getHostName()+
" and its address is: "+
myDetails.getHostAddress());
}
catch(UnknownHostException e){
System.err.println("Unknown host: "+e.getMessage());
}
}
else{
for(int i = 0; i < args.length; i++){
try{
InetAddress details = InetAddress.getByName(args[i]);
System.out.println("The host is called: "+
details.getHostName()+
" and its address is: "+
details.getHostAddress());
}
catch(UnknownHostException e){
System.err.println("Unknown host: "+e.getMessage());
}
}
}
}
} - When/if I show it to you running on my laptop, it only
says lamely the standard localhost address, but here's what
it did on my desktop donkeys' years ago when I first wrote
these lecture notes (alas, ai.mit.edu is no more!):
[jjb@jjb Networks]$ java PrintInetDetails
The local host is called: jjb.cs.bath.ac.uk and its address is: 172.16.33.1
[jjb@jjb Networks]$ java PrintInetDetails horsepower.ai.mit.edu soggy-fibers.ai.mit.edu
The host is called: horsepower.ai.mit.edu and its address is: 128.52.37.26
The host is called: soggy-fibers.ai.mit.edu and its address is: 128.52.32.78
[jjb@jjb Networks]$ java PrintInetDetails wjh.harvard.edu www.google.com
The host is called: wjh.harvard.edu and its address is: 140.247.94.249
The host is called: www.google.com and its address is: 66.102.11.99 - Notice that the two MIT AI lab addresses are very similar, as you'd expect.
V. Summary
- Don't forget about Buffers!
- A lot of examples of clients & servers
- A little bit of a feel for how to
use unix/linux, and
- how telnet can be used to fake one side of a client. Important for your coursework!
- About protocols, layers & the Internet
- And something about how security is changing...
- Of course, there's loads more to this story
- For example, look at the notes I linked to above for pictures of packets.
- Or take networking in your final year!
page author: Joanna Bryson
20 March 2014